
Protecting Your iPhone: Outsmarting Thieves & Device Lockouts
Protecting your iphone outsmarting thieves and device lockouts – Protecting Your iPhone: Outsmarting Thieves & Device Lockouts – In today’s digital age, our iPhones are more than just devices; they’re extensions of ourselves, holding our most precious data, memories, and connections. But with this convenience comes vulnerability, making our iPhones prime targets for thieves and device lockouts.
This guide equips you with the knowledge and strategies to safeguard your iPhone and its contents, ensuring you stay one step ahead of potential threats.
We’ll delve into the common ways thieves target iPhones, the different types of device lockouts, and real-world examples to illustrate the risks. Then, we’ll arm you with practical steps to secure your device, from setting strong passcodes to utilizing Find My iPhone and Activation Lock.
We’ll also explore data protection measures, including regular backups and encryption, to keep your sensitive information safe. Finally, we’ll discuss how to stay safe in public, respond to theft or lockout, and implement additional security measures to enhance your overall online security.
Understanding iPhone Security Risks
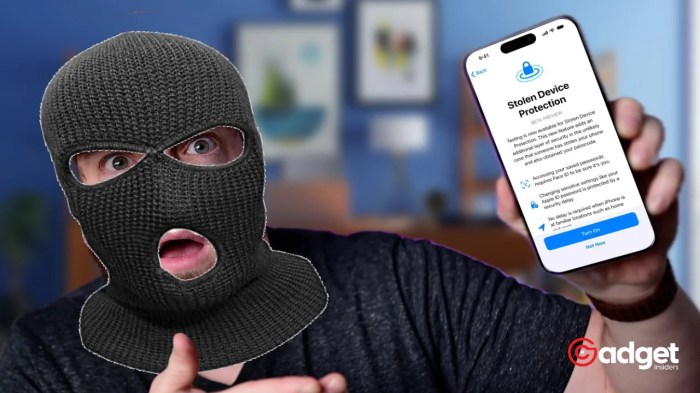
Your iPhone is a powerful device, but it’s not immune to security risks. Thieves and hackers are constantly devising new ways to exploit vulnerabilities, and understanding these threats is crucial to protecting your data and device.
Common iPhone Theft Tactics, Protecting your iphone outsmarting thieves and device lockouts
Thieves often employ a variety of tactics to target iPhones, often taking advantage of common user habits and vulnerabilities.
- Snatch-and-Grab:This involves a quick and forceful theft, usually in crowded areas or on public transportation. The thief might snatch the phone from your hand or pocket and run away.
- Distraction Theft:In this scenario, a thief will distract you with a request for help or a seemingly harmless interaction, allowing them to steal your phone without you noticing.
- Fake Repair Shops:Some thieves pose as legitimate repair technicians, offering to fix your phone at a lower price. They might steal your phone or copy your data during the “repair” process.
- Phishing Scams:These scams involve fraudulent emails, text messages, or websites that trick you into revealing personal information, such as your Apple ID password or credit card details.
Types of Device Lockouts
Device lockouts can occur for various reasons, each with its own implications.
- Passcode Lockout:After entering an incorrect passcode too many times, your iPhone will be locked, and you might need to reset it to regain access. This can lead to data loss if you haven’t backed up your device.
- Activation Lock:This feature, enabled through Find My iPhone, prevents anyone from using your device without your Apple ID and password, even if the phone is reset. This is a powerful security measure, but it can also lead to problems if you forget your Apple ID or password.
Protecting your iPhone from thieves and device lockouts goes beyond just a strong passcode. You also need to be mindful of your privacy, which is why understanding what is a privacy policy and why is it important is crucial. A privacy policy outlines how apps collect and use your data, which can be valuable information for thieves looking to exploit vulnerabilities.
By being aware of what data you’re sharing, you can make informed choices to protect your device and personal information.
- Account Lockout:If you enter the wrong Apple ID password too many times, your account may be locked, preventing you from accessing your device, apps, and other Apple services.
Real-World Examples of iPhone Theft and Lockout Scenarios
Understanding real-world scenarios can help you visualize how these risks can manifest.
- A tourist in a crowded market has their iPhone stolen by a snatch-and-grab thief.The tourist loses access to their photos, contacts, and important information, and the thief can potentially sell the phone or use it to access their accounts.
- A user forgets their passcode and repeatedly tries different combinations, resulting in a passcode lockout.They lose access to their data and may need to reset their phone, potentially losing all their information if they haven’t backed up.
- A user buys a used iPhone without knowing it has Activation Lock enabled.They are unable to use the phone as it’s locked to the previous owner’s Apple ID, and they might be unable to contact the previous owner to disable the lock.
Implementing Strong Security Measures
A strong iPhone security setup is the first line of defense against theft and unauthorized access. By implementing robust security measures, you can significantly reduce the risk of your personal data falling into the wrong hands.
Setting Up a Strong Passcode or Biometric Authentication
A strong passcode or biometric authentication acts as the primary barrier to accessing your iPhone. Here’s a step-by-step guide to setting up a secure authentication method:
- Choose a strong passcode:Avoid using common or easily guessable combinations. Opt for a passcode that is at least 6 digits long and includes a mix of numbers and symbols.
- Enable biometric authentication:Use Face ID or Touch ID for convenient and secure access. These features utilize your facial or fingerprint data to unlock your iPhone, providing a more secure alternative to a passcode.
- Avoid using the same passcode for multiple accounts:This minimizes the risk of compromise if one account is compromised.
- Enable “Erase Data After 10 Failed Attempts”:This setting ensures that your iPhone will automatically erase all data after ten consecutive failed passcode attempts, further safeguarding your information.
Benefits and Limitations of Find My iPhone and Activation Lock
Find My iPhone and Activation Lock are crucial security features that help you locate and protect your iPhone in case of loss or theft.
- Find My iPhone:This feature allows you to track your iPhone’s location on a map, remotely lock or erase its data, and even play a sound to help locate it. This can be particularly useful if you’ve misplaced your iPhone or if it’s been stolen.
- Activation Lock:This feature prevents anyone from using your iPhone even if they have your passcode. It requires your Apple ID and password to unlock the device, effectively rendering it useless to thieves.
While these features are powerful, it’s important to note their limitations:
- Find My iPhone requires a data connection:If your iPhone is offline or doesn’t have a data connection, you won’t be able to track its location.
- Activation Lock can be bypassed:While highly effective, Activation Lock can be bypassed by skilled hackers or with physical access to your iPhone.
Keeping Your iPhone Software Up-to-Date
Regularly updating your iPhone’s software is essential for maintaining its security. Software updates often include security patches that address vulnerabilities and bugs, which can be exploited by attackers.
- Enable automatic updates:This ensures that your iPhone automatically downloads and installs the latest software updates, keeping your device protected.
- Check for updates manually:If you haven’t enabled automatic updates, it’s essential to check for new software updates regularly.
- Install updates promptly:Don’t delay installing software updates, as waiting can leave your iPhone vulnerable to security threats.
Protecting Your Data and Privacy
Your iPhone holds a treasure trove of personal information, from financial details and sensitive communications to precious photos and memories. Safeguarding this data is paramount, and proactive measures are essential to ensure your privacy and security.
Protecting your iPhone from theft is more than just a physical lock; it’s about safeguarding your digital life. With the rising cost of everything, including new phones, understanding how to manage your finances is crucial. Check out the inflation guide tips to understand and manage rising prices to learn how to make your money go further.
Once you’ve got your finances in order, you can focus on securing your iPhone, knowing that you’re prepared for any unexpected expenses.
Data Backups
Regularly backing up your iPhone data is crucial for safeguarding your information. A backup allows you to restore your device to its previous state in case of loss, damage, or accidental deletion.
Just like you need to protect your iPhone from thieves and lockouts, it’s crucial to safeguard your financial future. Investing in the stock market can be a great way to grow your wealth, but it’s important to start with the basics.
Check out this guide for beginners to invest in the stock market and learn the basics. Similarly, securing your iPhone with a strong passcode and enabling Find My iPhone can prevent unauthorized access and help you recover your device if it’s lost or stolen.
- iCloud Backup:iCloud offers a convenient way to back up your data wirelessly. It automatically stores your data, including apps, settings, and photos, in Apple’s cloud storage. To set up iCloud backups, go to Settings > [Your Name] > iCloud > iCloud Backup and toggle it on.
You can choose to back up your device over Wi-Fi or cellular data.
- iTunes Backup:If you prefer a wired backup, iTunes allows you to create a complete backup of your iPhone to your computer. Connect your iPhone to your computer, open iTunes, and select your device. Click on “Back Up Now” to start the backup process.
- Third-Party Backup Services:Numerous third-party services, such as Google Drive, Dropbox, and OneDrive, provide cloud storage solutions for backing up your iPhone data. These services offer flexible storage options and may provide additional features, such as file synchronization and version history.
Protecting Sensitive Information
While backups safeguard your data, it’s equally important to protect sensitive information stored on your device.
- Use Strong Passwords:Employ strong, unique passwords for all your accounts, including your Apple ID and any apps that store sensitive data. A strong password consists of a combination of uppercase and lowercase letters, numbers, and symbols.
- Enable Two-Factor Authentication:Two-factor authentication adds an extra layer of security by requiring a code sent to your phone or email in addition to your password. This significantly reduces the risk of unauthorized access.
- Limit App Permissions:Carefully review app permissions when installing new apps. Only grant permissions that are absolutely necessary for the app to function. Avoid granting access to sensitive data, such as contacts, location, and photos, unless it’s essential.
- Use a Secure Browser:When browsing the web, use a secure browser, such as Safari or Chrome, that encrypts your data and protects your privacy. Avoid using public Wi-Fi networks without a VPN, as these networks are more susceptible to security breaches.
- Disable Location Services:While location services can be useful for navigation and location-based apps, it’s important to limit their use when not necessary. Disabling location services for apps that don’t require it can help protect your privacy.
- Avoid Sharing Personal Information:Be cautious about sharing personal information online, especially on social media platforms. Avoid posting sensitive details like your home address, phone number, or financial information.
Data Encryption Methods
Data encryption plays a vital role in protecting your privacy by converting your data into an unreadable format. iPhones offer several encryption methods to secure your data.
| Encryption Method | Description | Security Level |
|---|---|---|
| Device Encryption | Encrypts all data stored on your iPhone, including apps, photos, and messages. | High |
| FileVault | Encrypts data stored on your Mac, including your iPhone backups. | High |
| iCloud Keychain | Encrypts your passwords and other sensitive information stored in your iCloud account. | High |
| Data Protection API | Allows developers to encrypt sensitive data within their apps. | High |
“Data encryption is essential for safeguarding your privacy and protecting your information from unauthorized access.”
Staying Safe in Public

Your iPhone is a valuable tool, but it can also be a target for thieves and scammers, especially in public spaces. Staying vigilant and taking proactive steps can help you protect your device and your data.
Public Wi-Fi Precautions
Public Wi-Fi networks are convenient but often lack the security measures found on private networks. Using these networks can expose your data to potential risks. Here are some precautions to take:
- Avoid sensitive activities like online banking or shopping on public Wi-Fi.
- Use a virtual private network (VPN) to encrypt your internet traffic and protect your data.
- Enable your iPhone’s “Wi-Fi Assist” feature to automatically switch to cellular data when Wi-Fi is weak or unreliable.
- Be wary of public Wi-Fi networks with unusual names or those that do not require a password.
Spotting and Avoiding iPhone Scams
Scammers often target iPhone users with phishing emails, text messages, or fake apps. Being aware of common scams can help you protect yourself.
- Phishing Emails:Be suspicious of emails asking for personal information, such as your Apple ID password or credit card details. Never click on links in suspicious emails or open attachments from unknown senders.
- Text Message Scams:Be wary of text messages offering deals that seem too good to be true, or those asking for your personal information. Never reply to these messages or click on any links they provide.
- Fake Apps:Download apps only from the official App Store. Be wary of apps that promise unrealistic features or ask for unnecessary permissions.
Responding to Theft or Lockout: Protecting Your Iphone Outsmarting Thieves And Device Lockouts
It’s never pleasant to think about, but having your iPhone stolen or locked out can be a stressful experience. Knowing what to do in these situations can help minimize the damage and recover your device.
Contacting Your Carrier and Apple Support
If your iPhone is stolen or locked out, contacting your carrier and Apple Support is crucial.
- Contacting Your Carrier:Your carrier can help you suspend service to your stolen iPhone, preventing unauthorized use and potential financial losses. They may also be able to assist with reporting the theft to law enforcement.
- Contacting Apple Support:Apple Support can help you remotely lock or erase your iPhone, protecting your data. They may also provide information about device recovery options and replacement programs.
Reporting iPhone Theft to Law Enforcement
Reporting iPhone theft to law enforcement is essential for several reasons.
- Filing a Police Report:A police report is necessary for insurance claims and can help track down your stolen device. It also serves as documentation for any future legal actions.
- Utilizing Law Enforcement Resources:Law enforcement agencies often have resources and expertise in recovering stolen electronics. They may also have access to databases that can help identify the thief or locate your device.
Utilizing “Find My iPhone”
“Find My iPhone” is a valuable tool for locating and securing your iPhone.
- Locating Your Device:If you’ve enabled “Find My iPhone” on your device, you can use the app or website to locate your iPhone on a map.
- Remotely Locking or Erasing Your Device:You can use “Find My iPhone” to remotely lock your device with a passcode or erase all data to protect your personal information.
Additional Security Considerations

While implementing strong passwords and robust security measures on your iPhone is crucial, it’s equally important to extend these practices to your online accounts and digital footprint. This section delves into additional security considerations that contribute to a comprehensive approach to protecting your privacy and data.
Using Strong Passwords for All Online Accounts
Strong passwords are the first line of defense against unauthorized access to your online accounts. A strong password is a combination of uppercase and lowercase letters, numbers, and symbols, making it difficult for hackers to guess or crack. It’s also recommended to avoid using personal information like your name, birthdate, or pet’s name in your passwords.
Benefits of Using a Password Manager
Managing multiple strong passwords across various accounts can be challenging. Password managers offer a solution by securely storing your passwords and allowing you to access them with a single master password. This simplifies password management while maintaining strong security.
- Enhanced Security:Password managers encrypt your passwords, protecting them even if your device is compromised.
- Convenience:You only need to remember one master password to access all your accounts.
- Unique Passwords:Password managers encourage using unique passwords for each account, reducing the risk of compromise if one account is breached.
Here are some reputable password managers:
- LastPass:A popular choice with a free tier and paid options for advanced features.
- 1Password:Known for its user-friendly interface and strong security features.
- Dashlane:Offers a comprehensive suite of features, including a VPN and identity theft protection.
Protecting Your Online Identity and Avoiding Phishing Scams
Protecting your online identity is paramount in today’s digital landscape. Phishing scams are a common tactic used by cybercriminals to steal personal information, such as login credentials and credit card details.
- Be Cautious of Suspicious Emails and Links:If you receive an email from an unknown sender or a link that seems suspicious, avoid clicking on it.
- Verify the Sender’s Identity:Before providing any personal information, double-check the sender’s email address and website.
- Beware of Urgent Requests:Be wary of emails or messages demanding immediate action or threatening consequences.
- Enable Two-Factor Authentication:Two-factor authentication adds an extra layer of security by requiring a code sent to your phone or email in addition to your password.
- Use a Separate Email Address for Online Accounts:This helps protect your primary email address from spam and phishing attempts.

